How to Set Up IP Filtering and DNS Blackholing on pfSense Using pfBlockerNG
What is pfBlockerNG?
pfBlockerNG has two core uses:
Inbound & outbound traffic filtering
pfBlockerNG can filter inbound and outbound traffic against IP lists and apply GeoIP restrictions by allowing or denying traffic to/from specific countries. The latter functionality can be very useful if you open ports on your WAN.
Blocking ads and malicious sites through DNS blackholing
pfBlockerNG can block ads and access to malicious sites through DNS filtering. Browsing the web, your DNS requests are checked against a blocklist. If there’s a match, the request is blocked. It’s a great way to block ads without using a proxy server.
We’re going to look at both use cases and will go into more detail as we tackle each one.
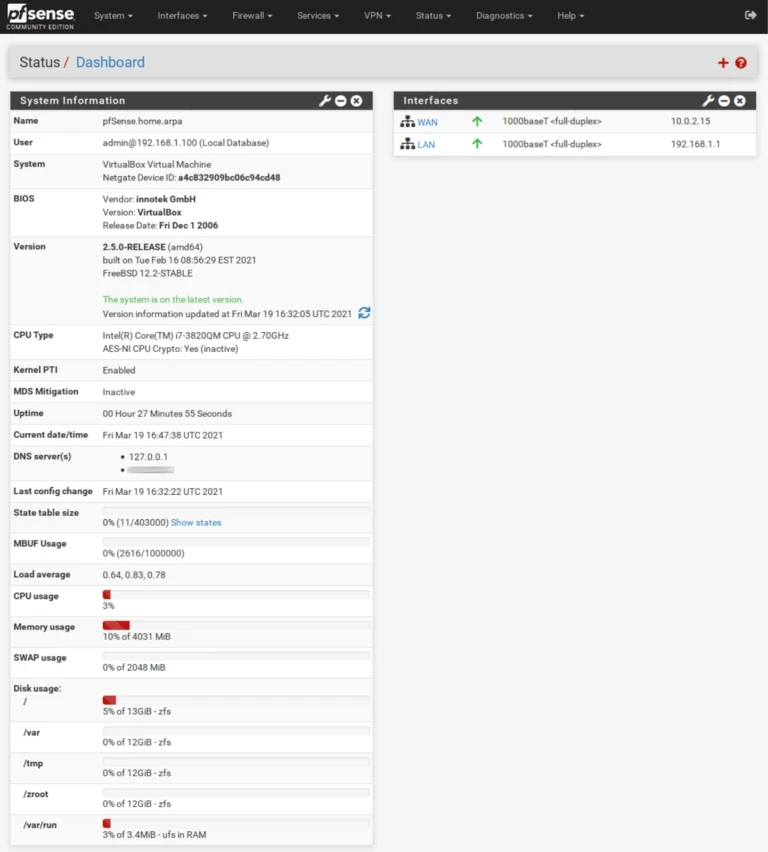
This guide assumes that you have already set up pfSense with functional WAN and LAN interfaces.
Let’s get started.
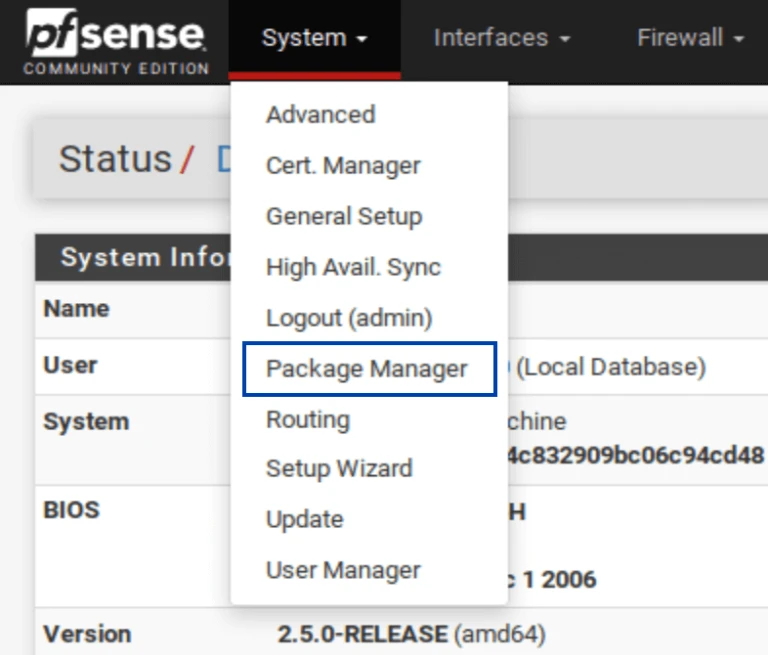
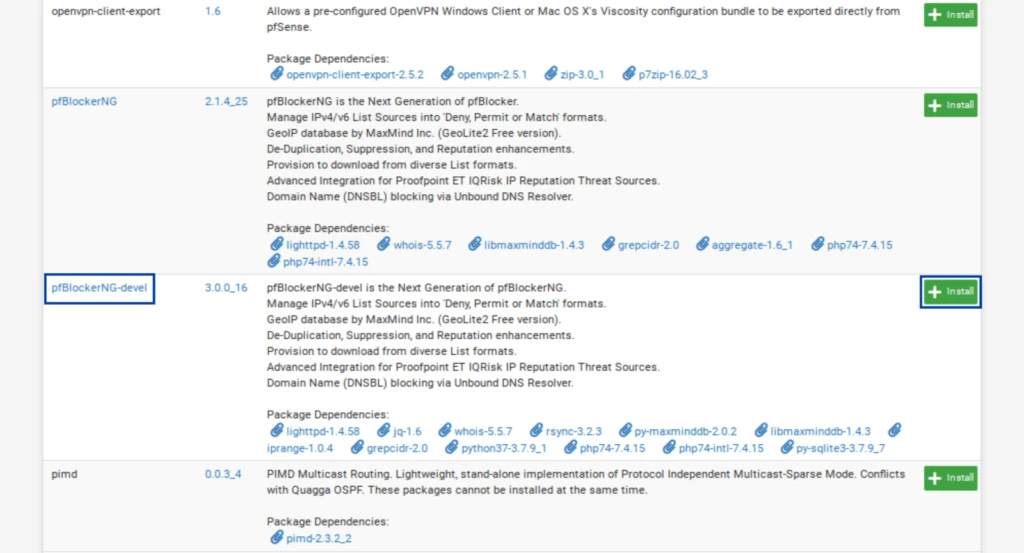
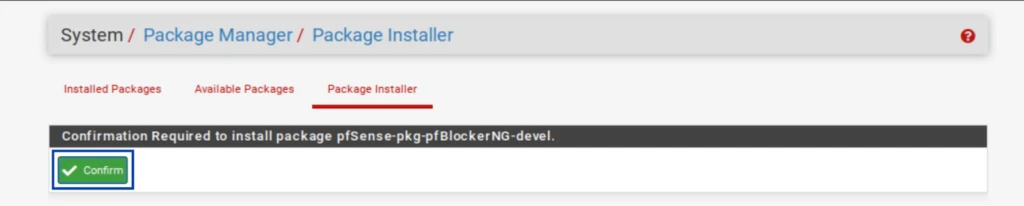
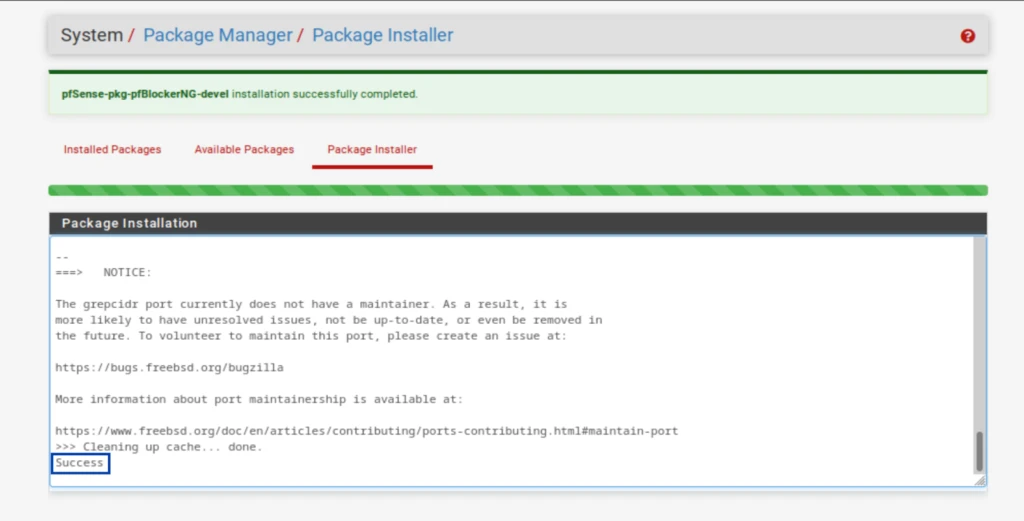
Installing pfBlockerNG-devel
The first thing we need to do is install pfBlockerNG.
Basic Setup
Now that pfBlockerNG-devel is installed, we need to configure our package. And we’re going to start with IP and GeoIP filtering.
We’ll be configuring pfBlockerNG section by section. Any settings that are not mentioned should be left at their default values.
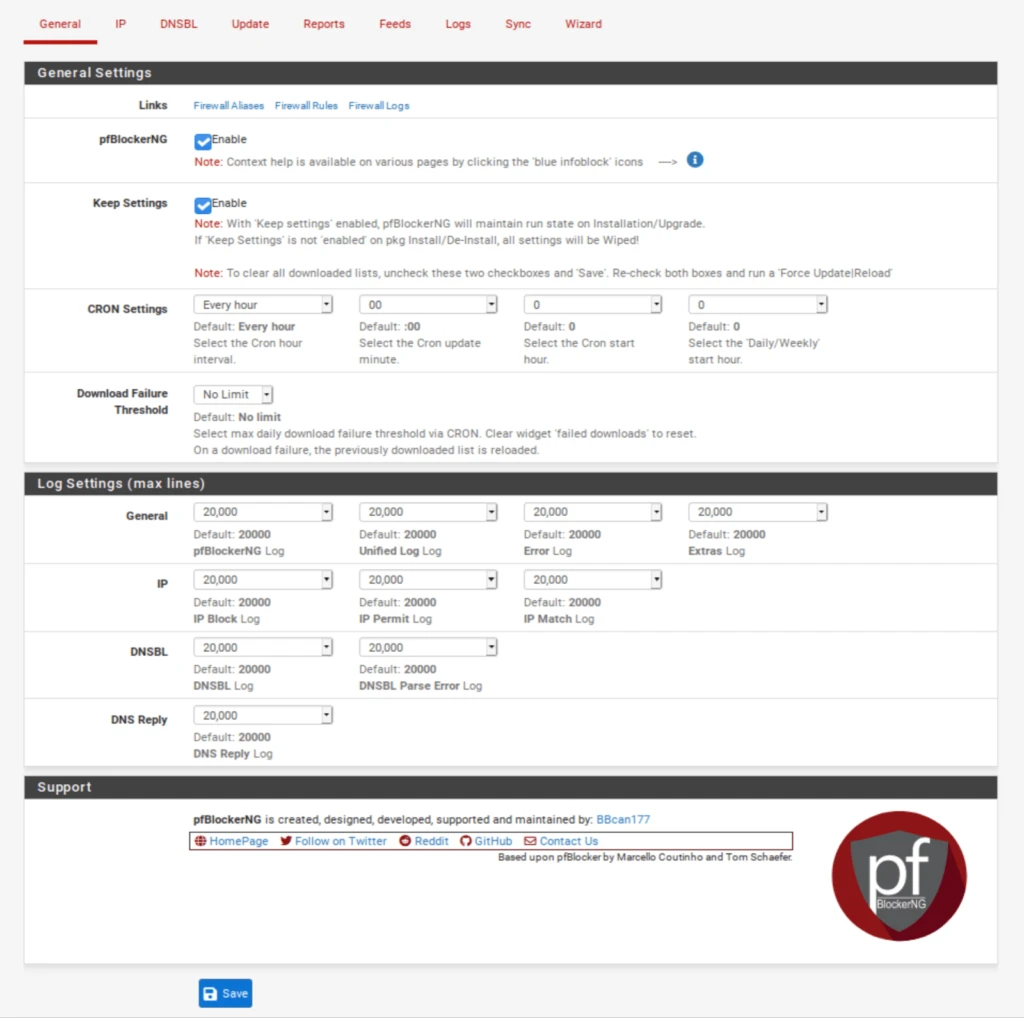
General / General Settings
- Check the Enable box displayed to the right of pfBlockerNG. This enables the service.
- Click Save at the bottom of the page.
- We will leave the other settings on this page at their default values.
IPv4 Filtering
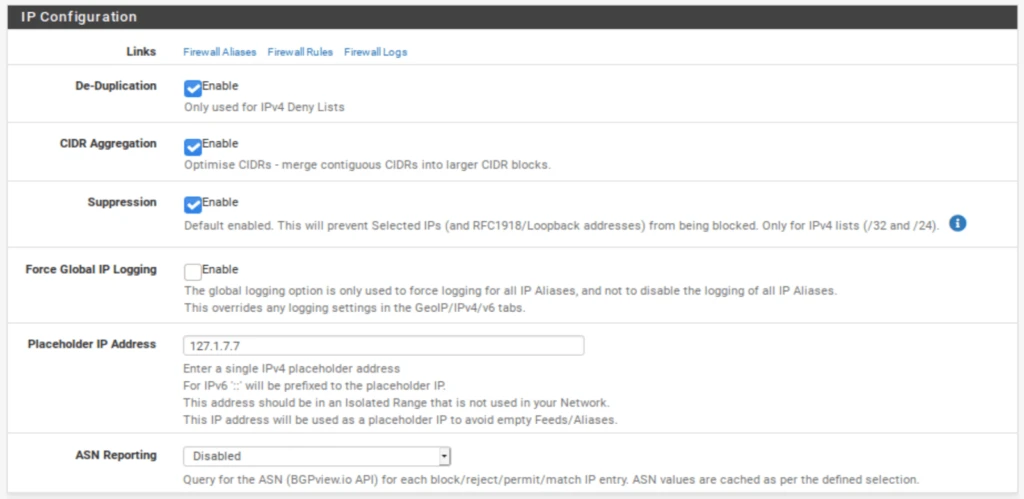
IP / IP Configuration
- Select the IP tab to access the IP settings page. Don’t touch the sub-menus that appear below for now.
- Enable De-Duplication. This will resorb duplicate entries if you are using multiple IP feeds.
- Enable CIDR Aggregation.
- Enable Suppression. Suppression makes sure that your local subnets are not blocked.
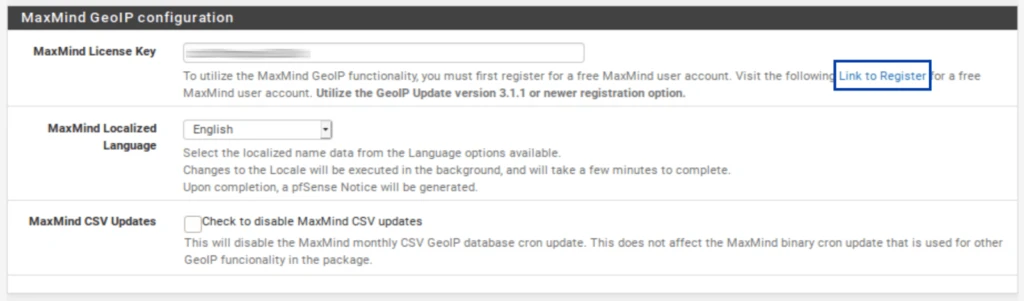
IP / MaxMind GeoIP configuration
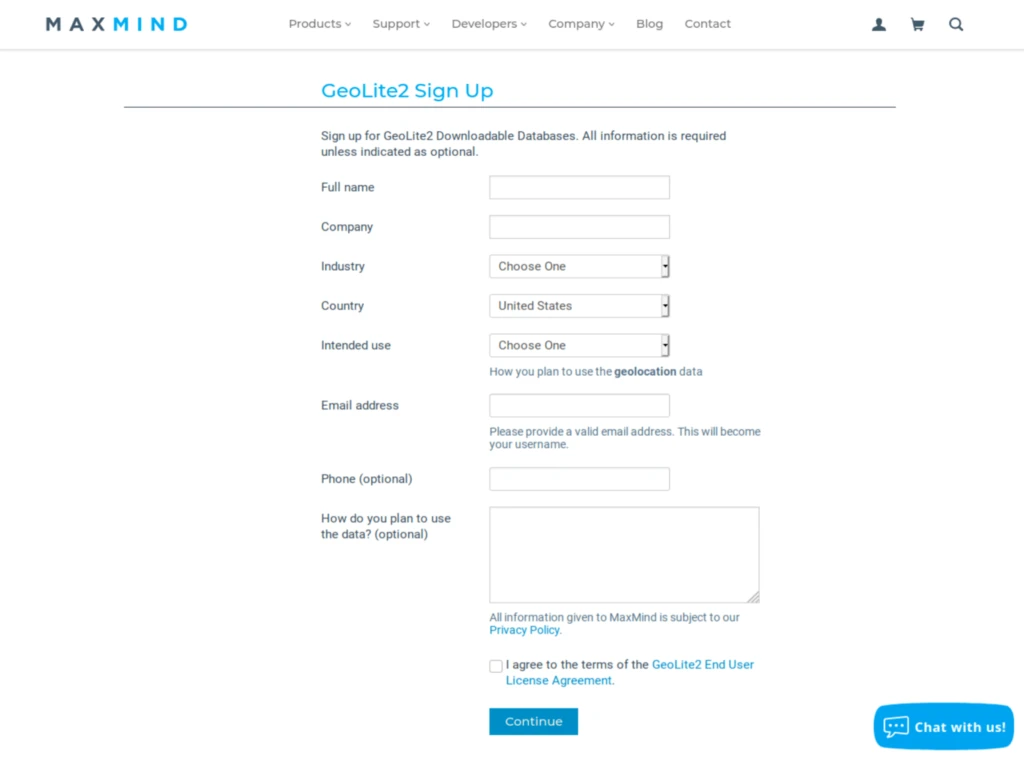
As I mentioned above, the GeoIP feature of pfBlockerNG enables you to filter traffic to and from entire countries or continents. To do this, pfBlocker uses the MaxMind GeoIP database, which requires a license key. A link in the MaxMind License Key field description takes you to the MaxMind registration page. The MaxMind license key is free.
Fill out the registration form to obtain your license key. Once you have your license key, insert it in the MaxMind License Key field.
And:
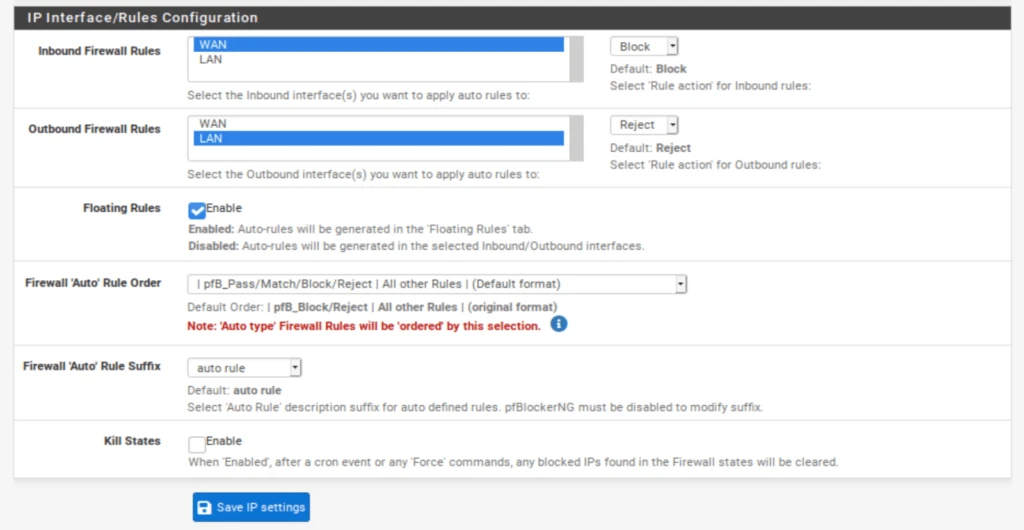
IP / IP Interface/Rules Configuration
This section determines which inbound and outbound interface(s) pfBlockerNG’s IPv4, IPv6, and GeoIP filtering are applied.
- Select WAN from the Inbound Firewall Rules field (and any other WAN interfaces you may have and want to filter).
- Select LAN from the Outbound Firewall Rules field (and any other LAN-type interfaces you may have and want to filter).
- Enable Floating Rules. Floating rules are special firewall rules applied before the regular firewall rules. This ensures that pfBlockerNG’s filtering happens as soon as the traffic hits the firewall. The other benefit is that pfBlockerNG will automatically create the floating rules for you.
- Click Save at the bottom of the page.
Adding IPv4 Feeds
It’s now time to add some blocklists to pfBlockerNG. While you’re free to add your custom feeds, pfBlockerNG has some built-in feeds we can enable (the terms list and feed are interchangeable in this context).
This is very practical because hunting down blocklists on the internet is time-consuming, and many do not work or are no longer maintained. The feeds within pfBlocker are live lists that are regularly updated, so we’re going to use those.
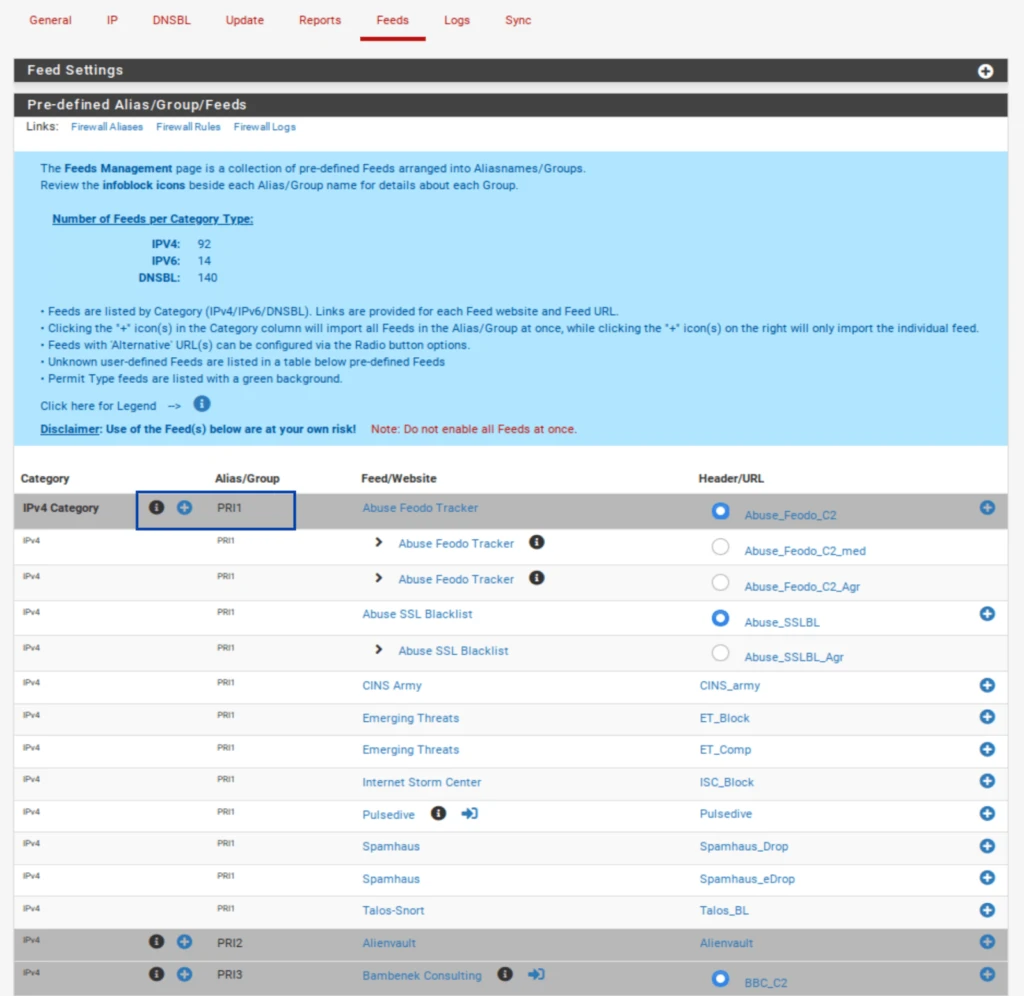
- Select the Feeds tab.
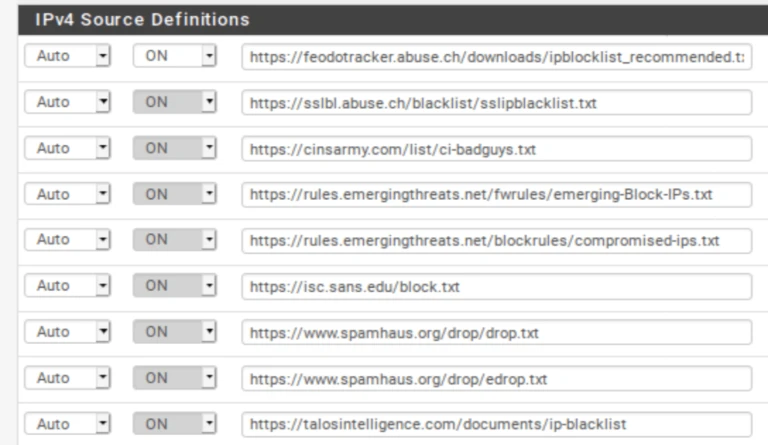
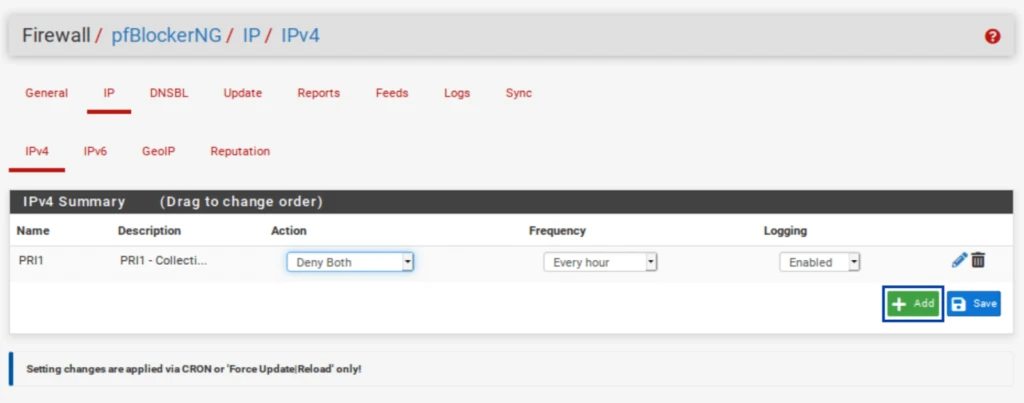
- Click the blue +, next to PRI1. It is the first listing. PRI1 is a collection of feeds, so it comprises several feeds, as we’ll see in a moment. Once you click the blue +, you’re taken to the IP / IPv4 page, where your selected feeds are listed. And almost all of the relevant fields are automatically populated.
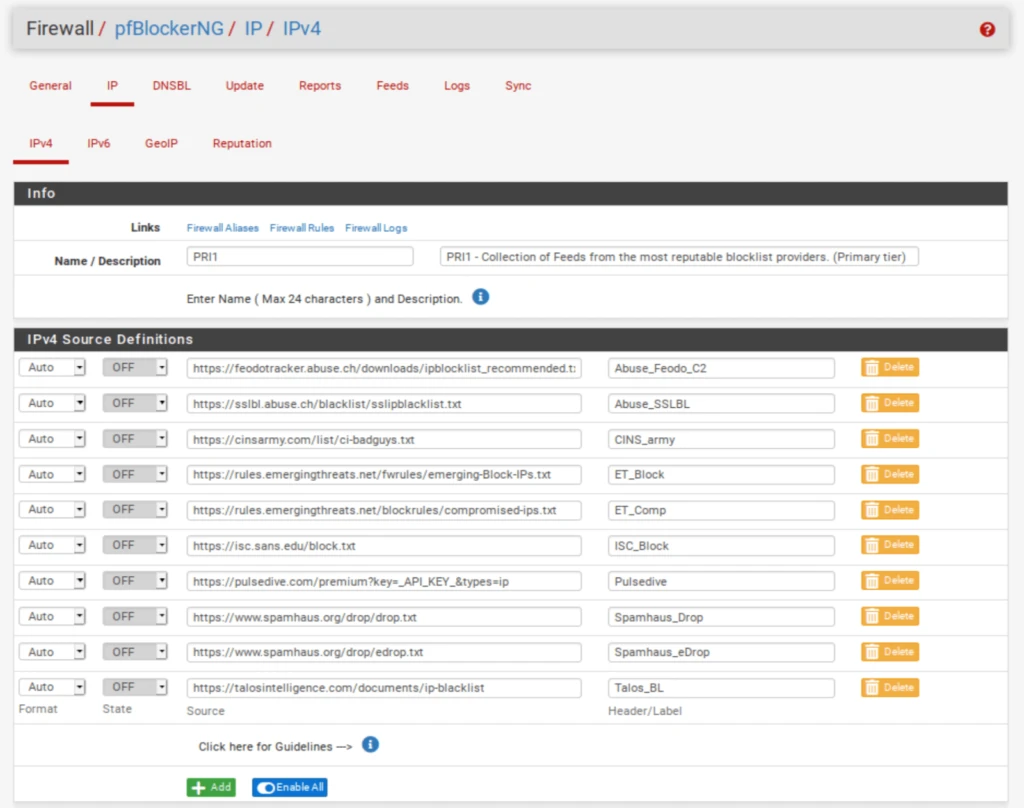
IP / IPv4
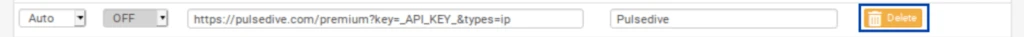
The name of the feed collection is populated along with its description. The feed URLs included in the collection and their associated descriptions are also populated. However, our feeds are set to OFF by default. We need to enable them.
But before doing that, we need to delete one of the feeds from the PRI1 collection. Pulsedive, the 7th feed from the top, is a premium list that requires a paid API key. We’re not going to get the API key for this tutorial. Click the Delete button.
- Once you’ve deleted Pulsedive, set all of the feeds to ON.
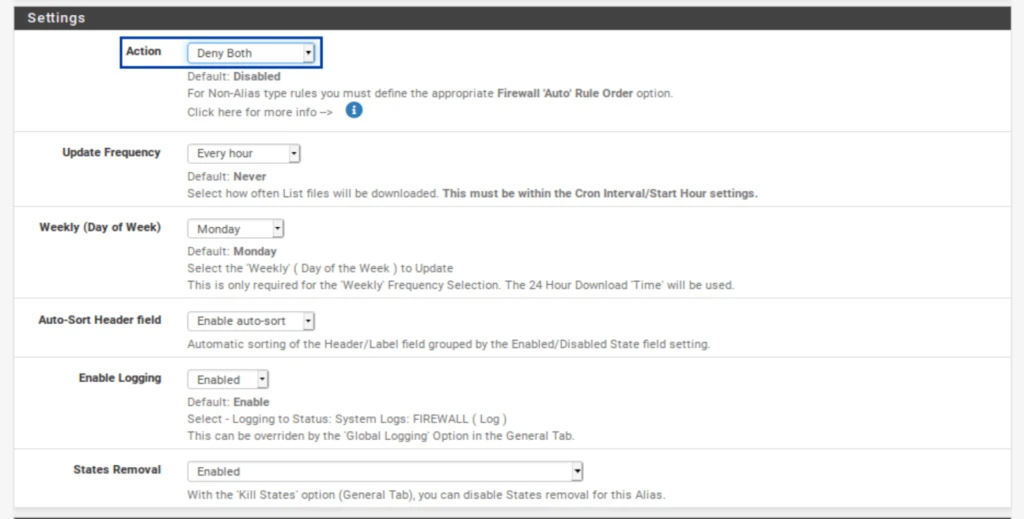
- Scroll down to the Settings section of the page.
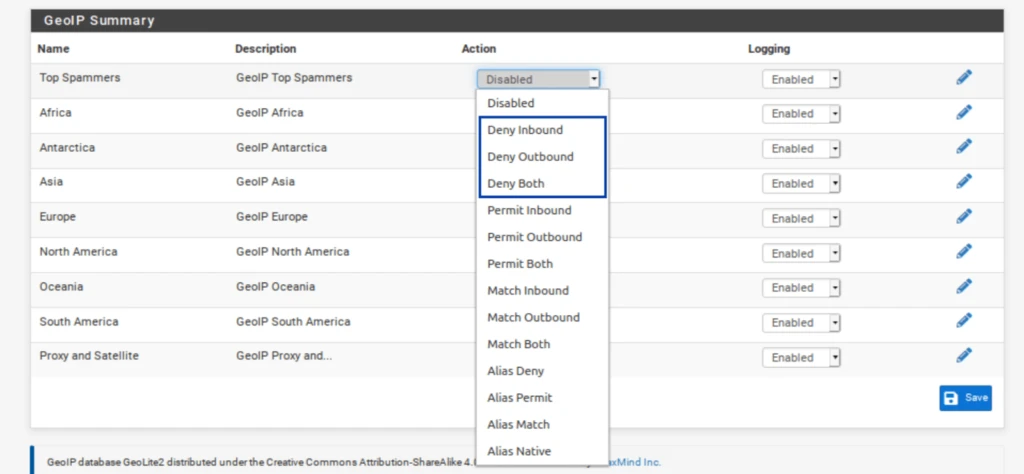
- From the Action drop-down menu, select Deny Both. This will block traffic to and from the IP addresses in the lists/feeds. You can choose only to deny inbound or outbound connections if you like. Just be warned that if you only deny inbound traffic and a host on your network initiates an outbound connection to one of those IPs, the inbound response from that IP will be allowed in. That may be fine depending on your environment – just be warned. For this example, I’m going to select Deny Both.
- Click Save IPv4 Settings at the bottom of the page.
You can repeat the same steps for IPv6 if your ISP assigns an IPv4 and an IPv6 IP address to your WAN. Most of us are still on IPv4-only networks.
GeoIP Filtering
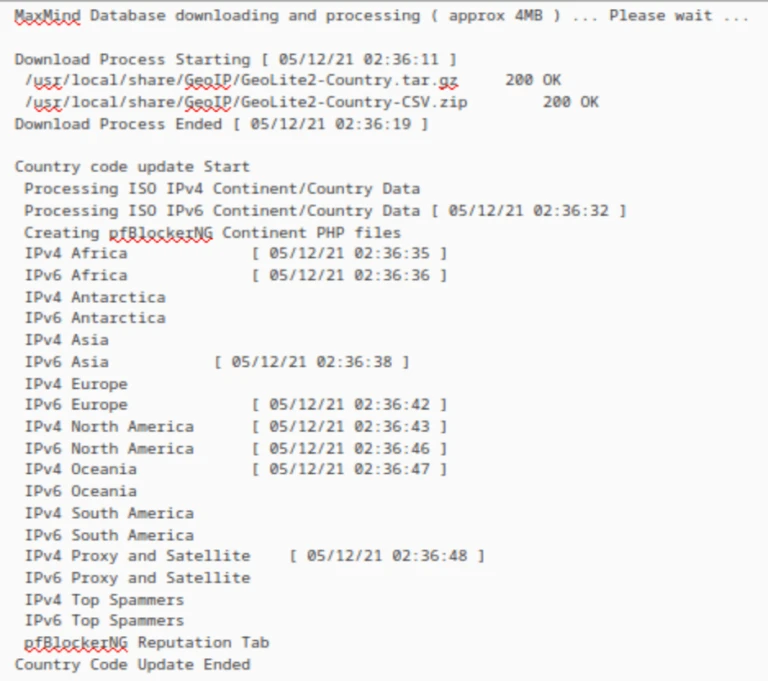
Before configuring GeoIP filtering, we first need to force an update of pfBlockerNG. pfBlocker automatically updates itself at fixed intervals. But to configure GeoIP filtering, pfBlocker first needs to pull the MaxMind database, and a forced update will do just that.
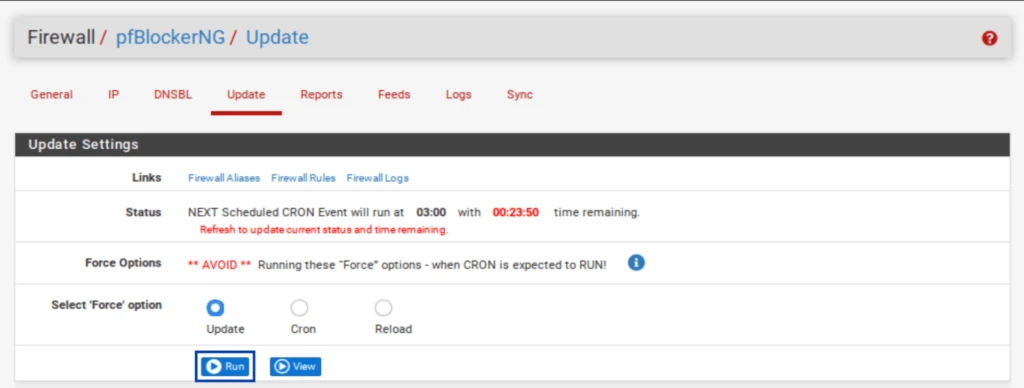
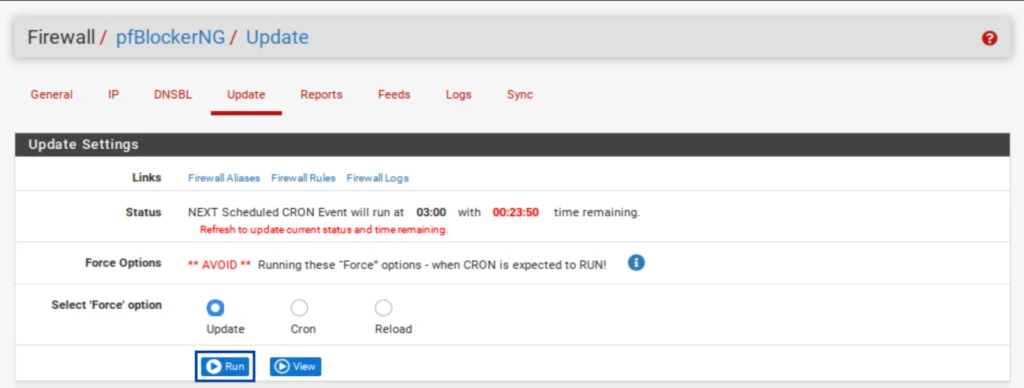
- Select the Update tab from the pfBlockerNG settings.
- Click Run. The update starts.
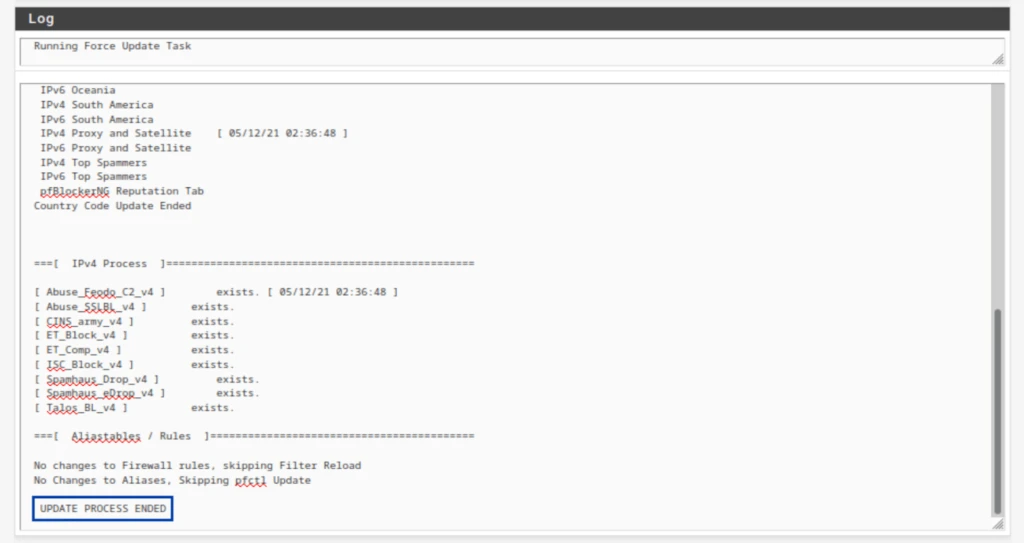
- Once the update is complete, you should see UPDATE PROCESS ENDED at the bottom of the Log window below the Update Settings.
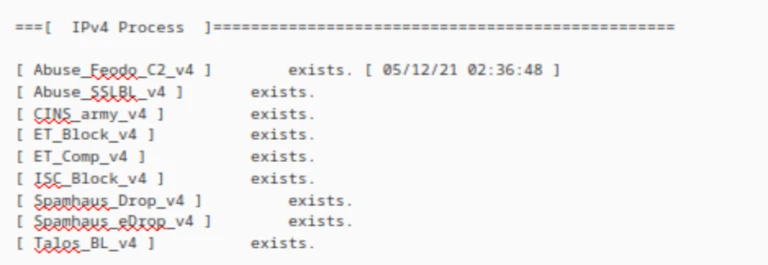
- Looking through the Log window, we can see that both my IPv4 feeds and the GeoIP database were updated.
IPv4 logs
GeoIP logs
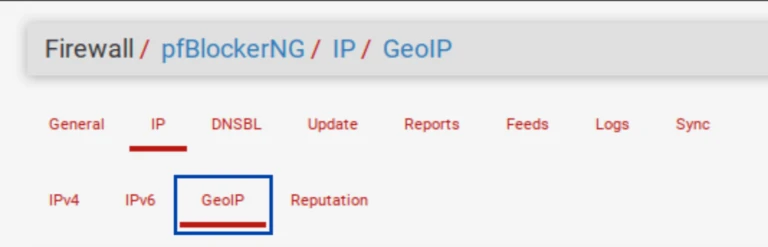
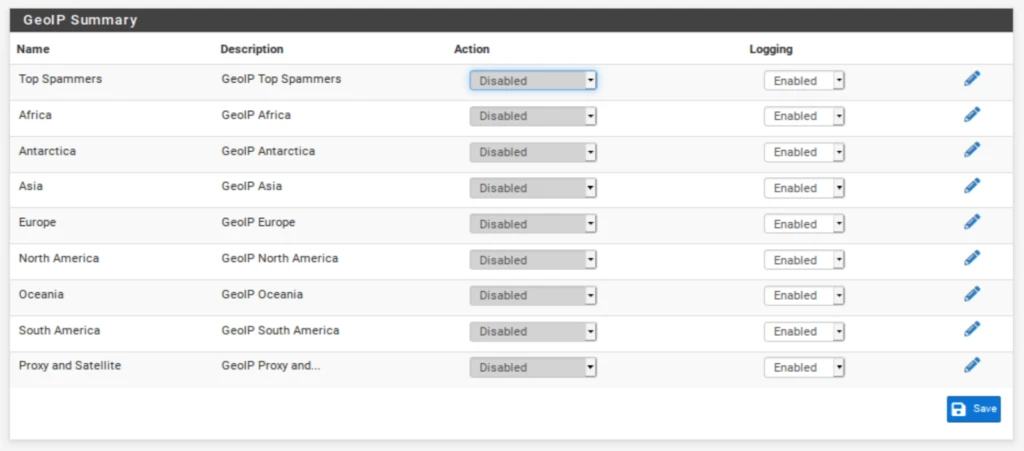
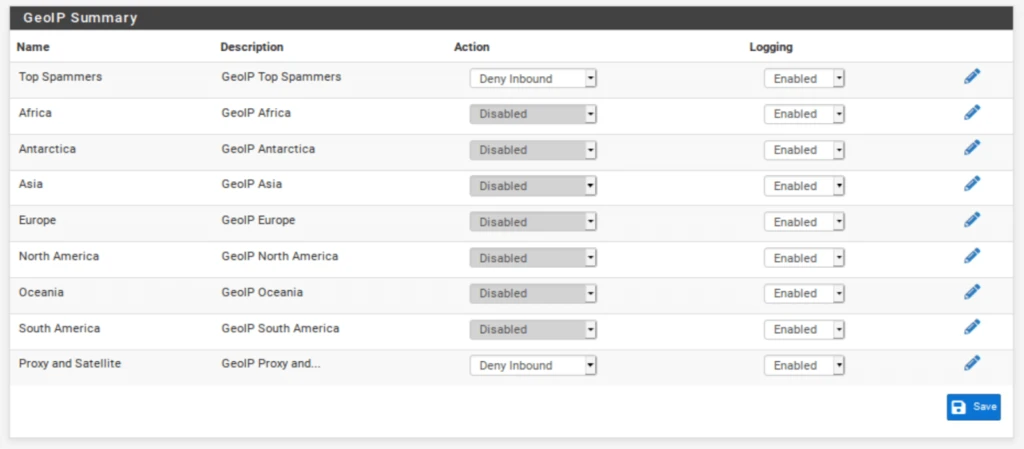
- From the IP tab in the pfBlockerNG settings, select the GeoIP sub-menu. The GeoIP Summary is displayed.
The GeoIP Summary consists of IP address feeds organized by continent, with two extra categories: Top Spammers and Proxy and Satellite. Top Spammers is a list of countries known to be a frequent source of online attacks. And Proxy and Satellite are known anonymous proxy and satellite providers.
You can filter traffic to/from an entire continent, or you can fine-tune the feed by selecting only the countries you want to filter.
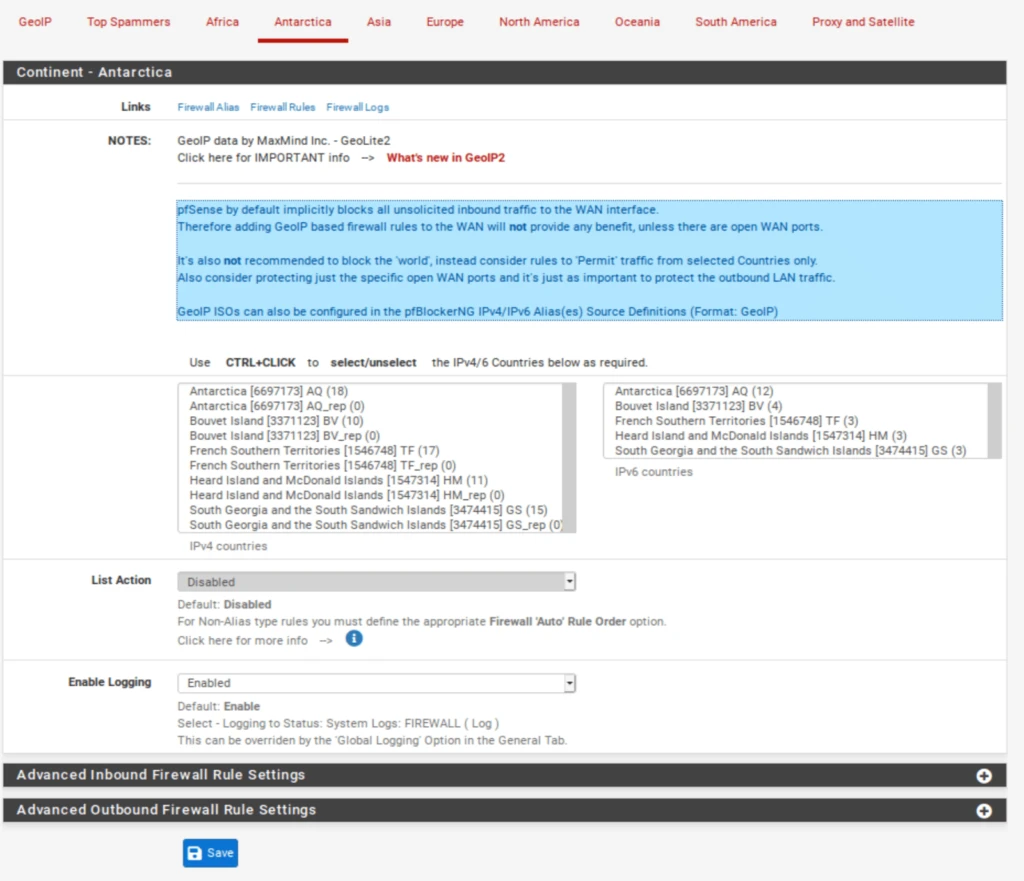
Customizing country lists
Configuring country blocks
Now, there are certain things to consider here. If you want to block outbound connections to a country or continent, go right ahead. However, if you’re thinking of blocking inbound links from a government or continent, consider that pfSense blocks all unsolicited inbound traffic on the WAN by default.
That means that unless you have open ports on your WAN, blocking countries or continents is useless and will only consume memory for nothing. If you have open ports on your WAN, make sure you don’t block connections from countries you want to allow to connect to your open port(s).
Aliases are IP address lists in themselves that are native to pfSense. Using aliases, you can allow only the specific countries you selected to access your open ports. However, there is a way to create custom aliases from the MaxMind GeoIP database within pfBlockerNG that can be used directly as the source in your port forwarding firewall rules.
Creating a GeoIP alias in pfBlockerNG
Because pfSense automatically blocks any traffic that isn’t explicitly allowed in the firewall rules, we want to create an alias of the countries we will allow through the firewall. pfSense will block the rest by default.
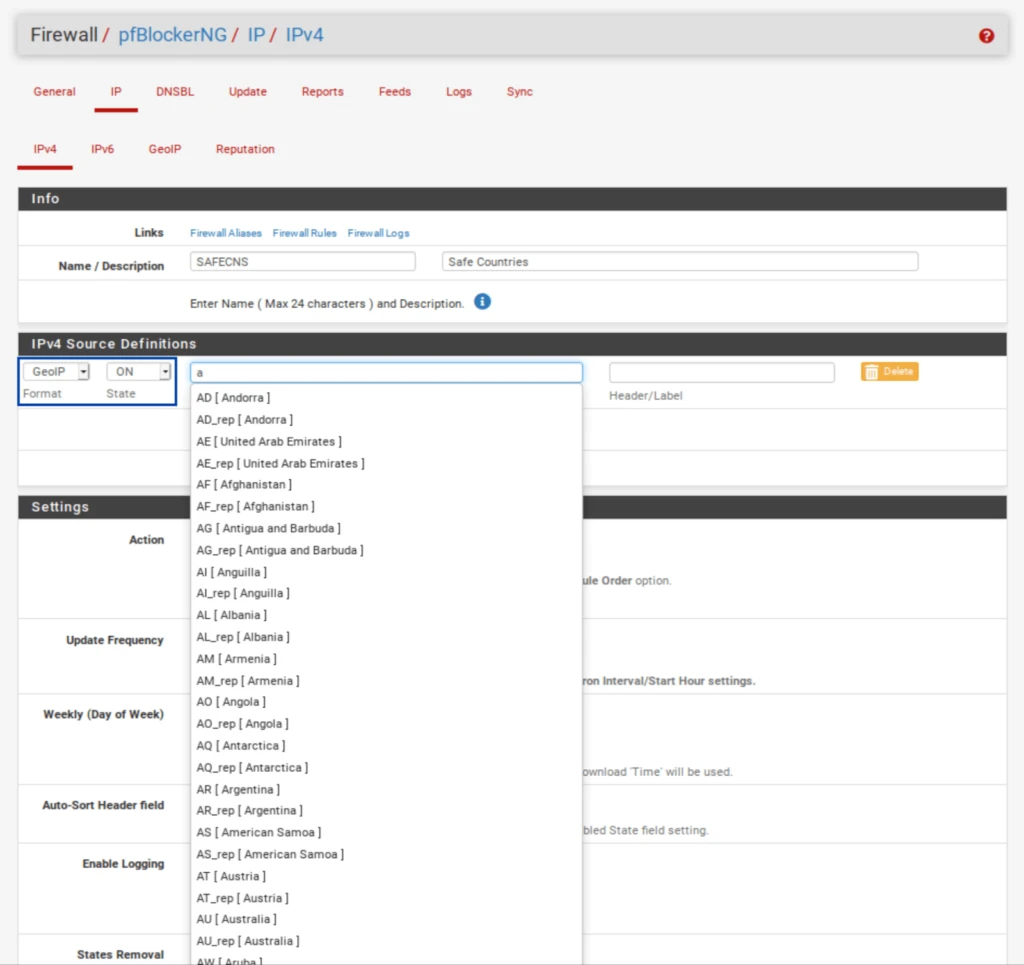
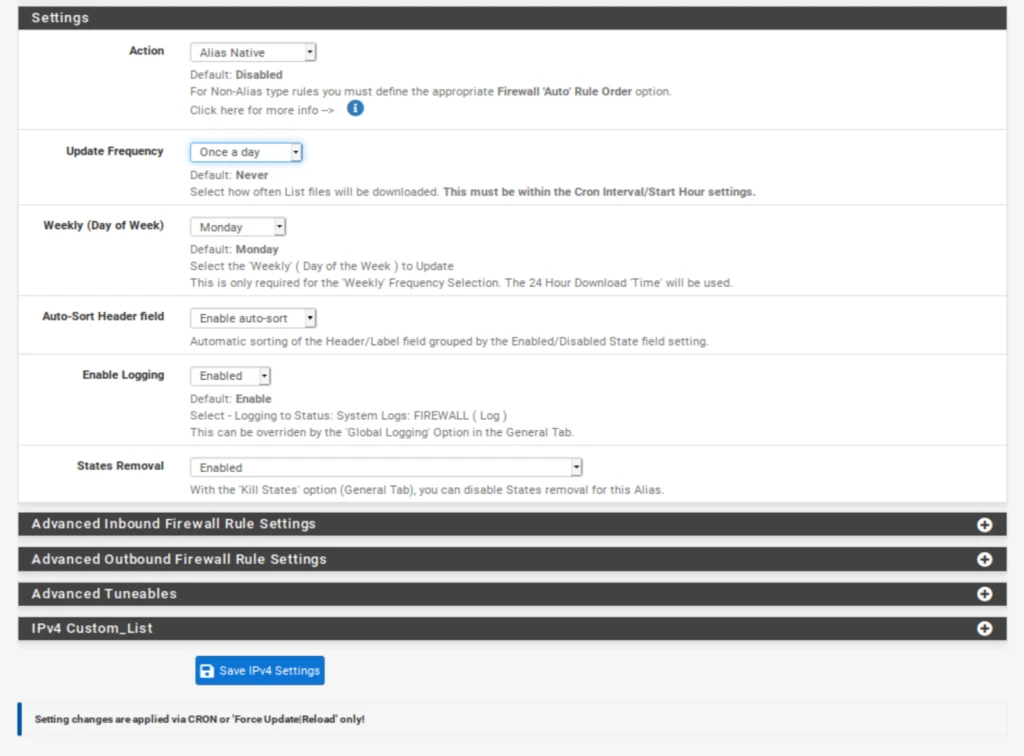
Set the Action to Alias Native.
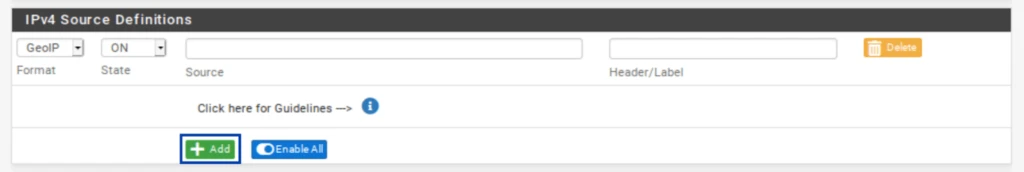
- Type the first letters of the country you want to add to the alias. Select the countries you wish to add to the alias. The list of countries appears.
- You can add more countries to your alias by clicking the green Add button.
- Set the Update Frequency to Once a day.
- Click Save IPv4 Settings at the bottom of the page. Once you force an update of pfBlockerNG, your alias will be available for inclusion in your firewall rules.
If you do have open ports but want to keep it simple, you can block inbound connections from Top Spammers and Proxy and Satellite without creating a custom alias. Remember that this is only useful if you have open ports on your WAN.
If you do not have any open ports on your WAN, only block outbound traffic or leave GeoIP filtering disabled.
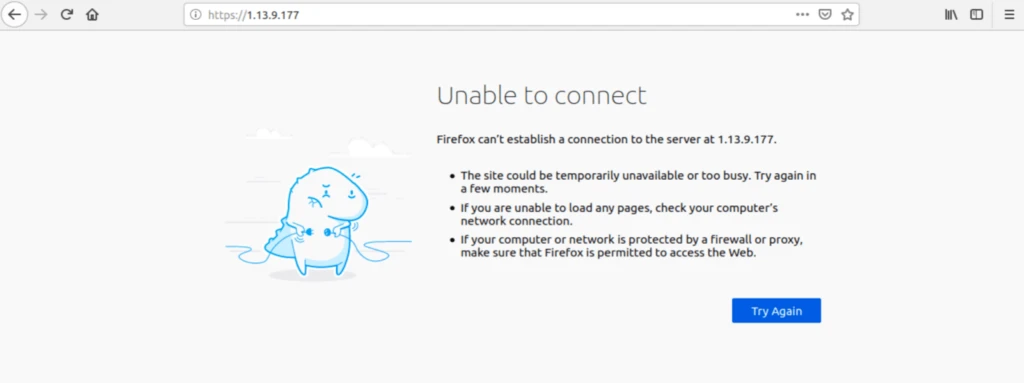
Testing IPv4 filtering
To make sure that our traffic is being filtered. We can try to connect to a known IP address in the blocklist. If I try to access 1.13.9.177 (an IP contained in my pfBlockerNG IPv4 feeds) in my browser, the IP address does not get translated to a domain name, and I cannot connect. That’s what we want.
Let’s move on to configuring pfBlocker’s DNSBL.
DNSBL
Alright. We’ve configured IPv4 filtering and GeoIP filtering, and aliases. It’s now time to move on to using pfBlockerNG for ad-blocking. Ad-blocking in pfBlockerNG is achieved through DNS blackholing. This references your DNS requests against a list of known ad networks and trackers and blocks them at the DNS level whenever there’s a match, resulting in an ad-free internet. Hooray.
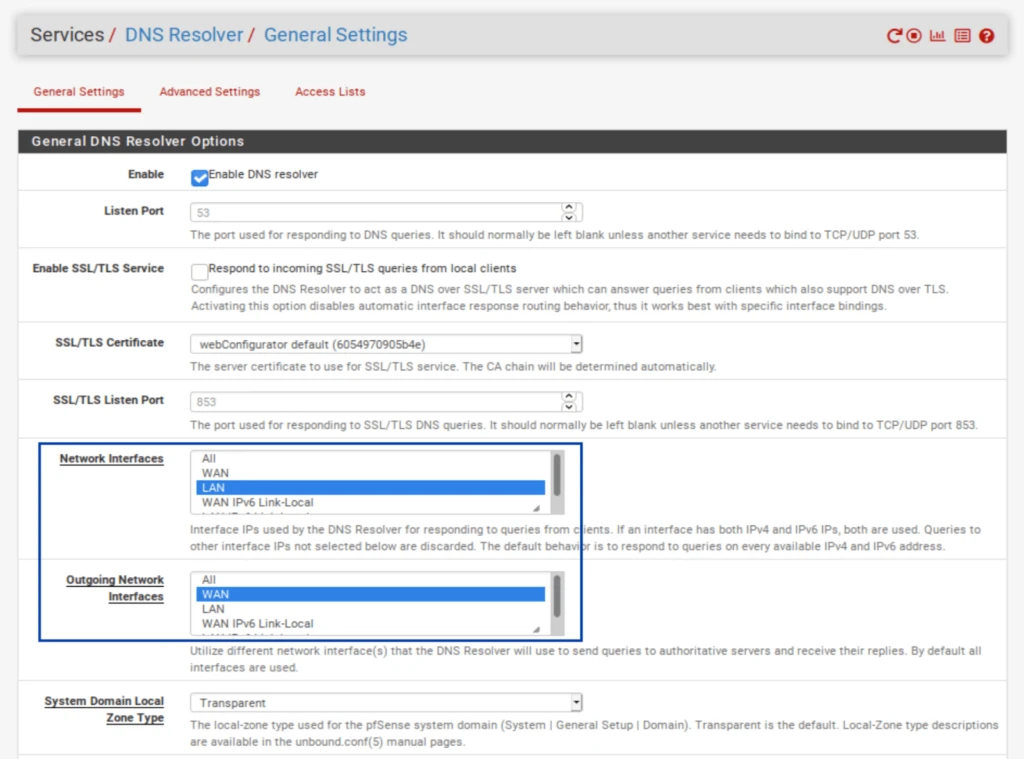
To use the DNSBL feature in pfBlockerNG, you must be using the DNS Resolver in pfSense for your DNS resolution. That means you can’t assign your hosts’ DNS via DHCP or use the DNS Forwarder (dnsmasq) if you want to use the DNSBL feature.
By default, pfSense uses the DNS Resolver on all interfaces. So if you didn’t make any changes to the DNS Resolver settings, you’re fine. If you made changes, configure the Resolver to bind to your LAN (outgoing) and your WAN (incoming). And select any other LAN-type (OPT interfaces) and WAN-type (multi-WAN setup, VPN gateways) interfaces you want the DNSBL to filter.
Configuring DNSBL
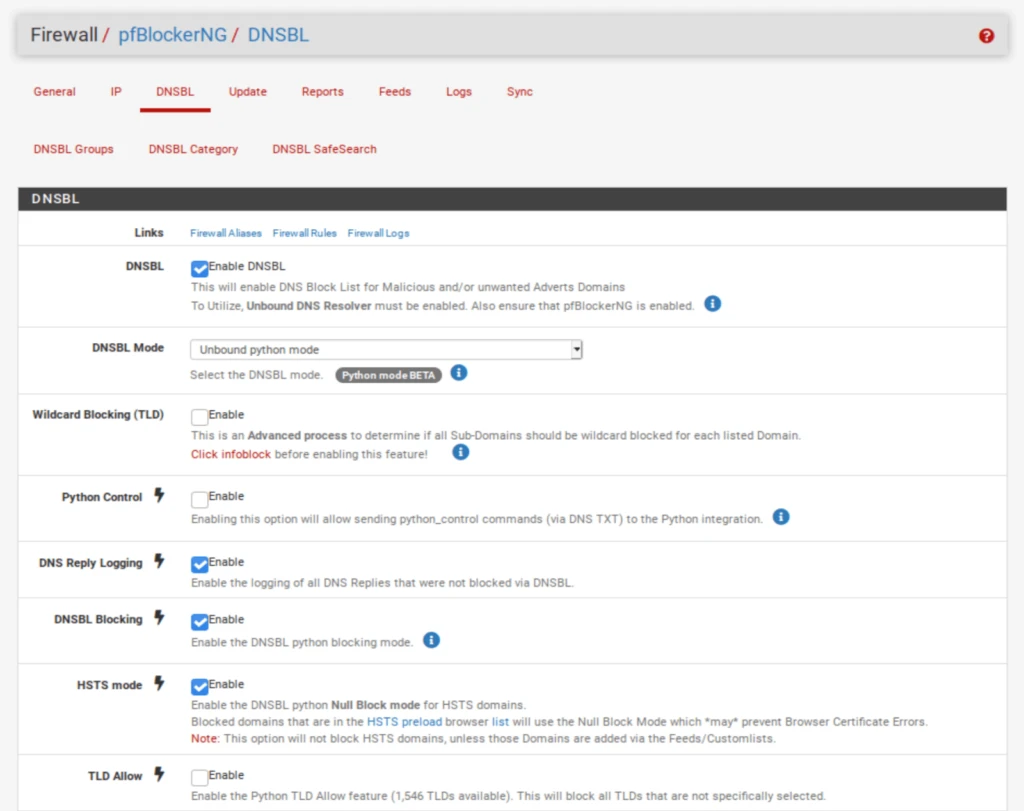
- Select the DNSBL tab.
- strong>Enable DNSBL.
- Next to DNSBL Mode, select Unbound Python mode.
- Scroll down to the DNSBL Configuration section.
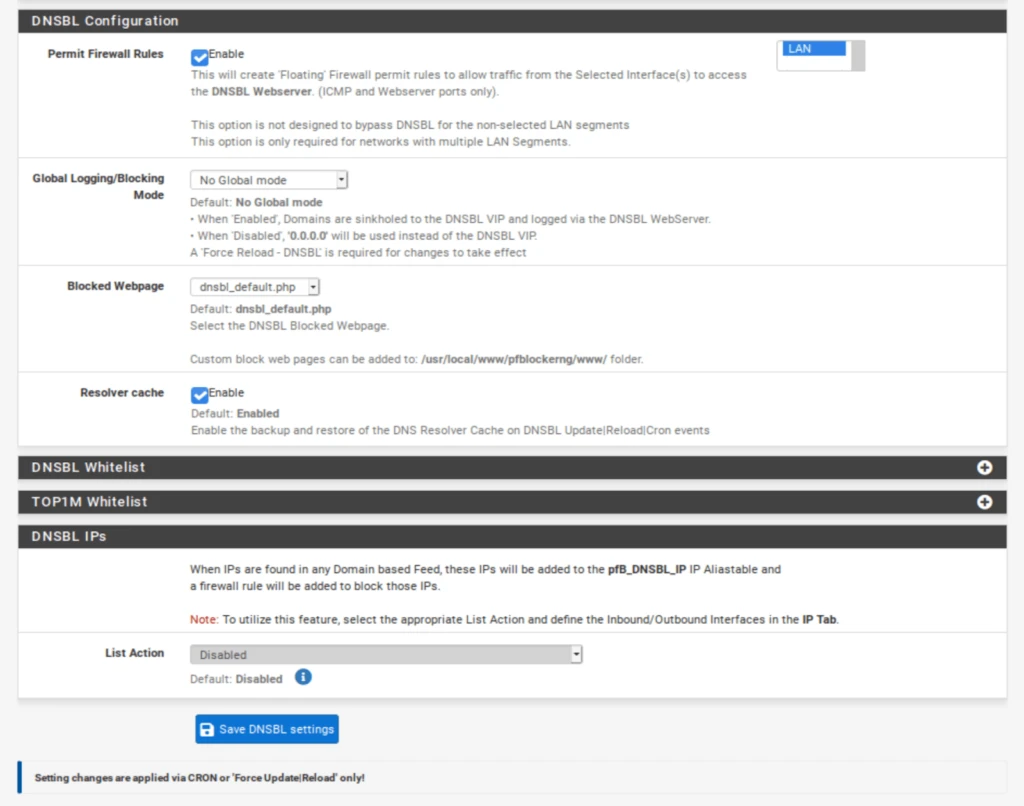
- Enable Permit Firewall Rules and select your LAN and any other LAN-type interfaces you want to filter with DNSBL. This will automatically create floating firewall rules (as we did with IPv4 filtering) so that DNSBL filtering will happen as soon as traffic hits the firewall.
- Click Save DNSBL settings at the bottom of the page.
We now need to add some DNSBL feeds.
Adding DNSBL feeds
- Select the Feeds tab.
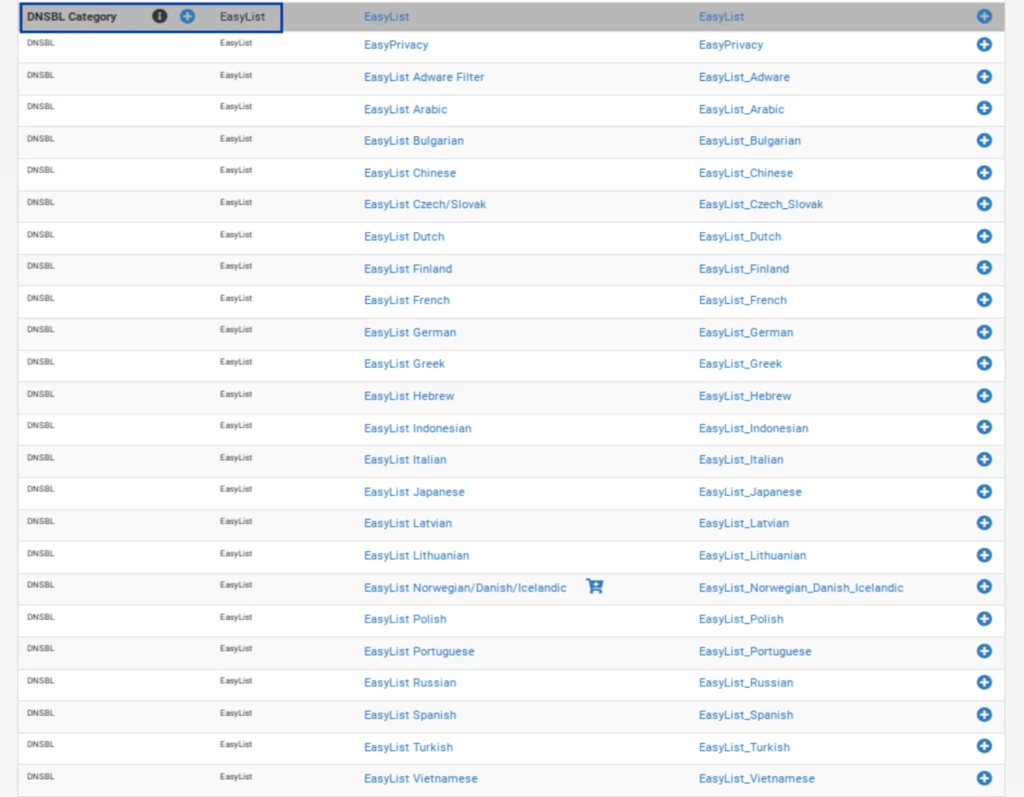
- Scroll down until you see DNSBL Category on the left. The first such entry is EasyList.
- Click the blue + to the left of EasyList. You’re taken to the DNSBL Groups page, where your selected feeds are listed, as with IPv4 filtering. And almost all of the relevant fields are automatically populated.
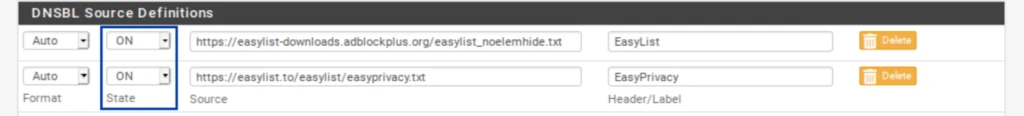
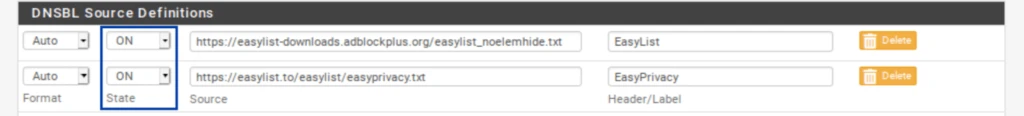
- Delete all of the feeds except the first and last one: EasyList and EasyList Privacy.
- Set the remaining feeds to ON.
- Scroll down to the Settings section.
- Set the Action to Unbound.
- Click the + to the right of DNSBL Custom_List. The DNSBL Custom_List window is displayed.
- Enter vungle.com in the DNSBL Custom_List window. We’re adding this domain so we can make sure DNSBL filtering is working by trying to access a known blocked domain.
- Click Save DNSBL Settings at the bottom of the page.
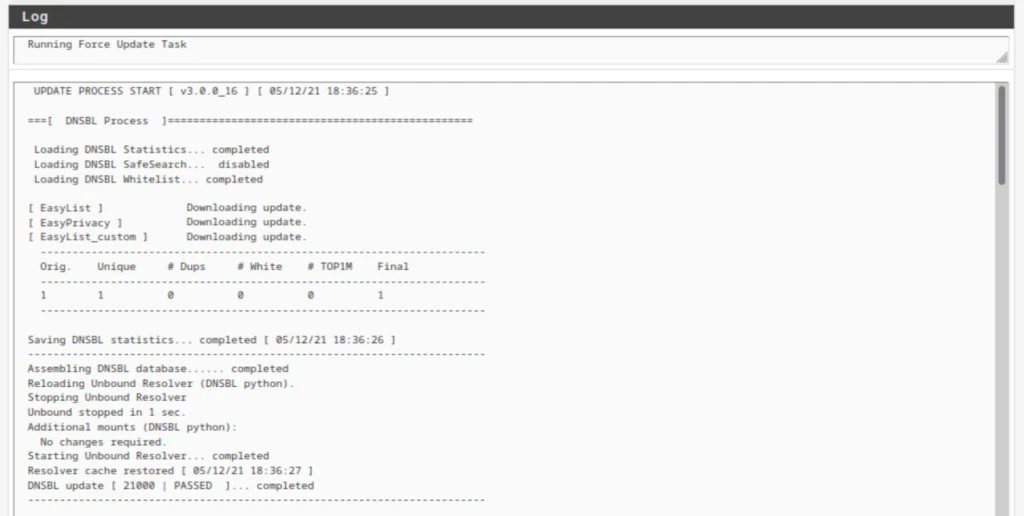
Forcing an update of pfBlockerNG
We now need to force an update of pfBlockerNG, as we did above.
Once the update is complete, we can see that our DNSBL feeds have been updated.
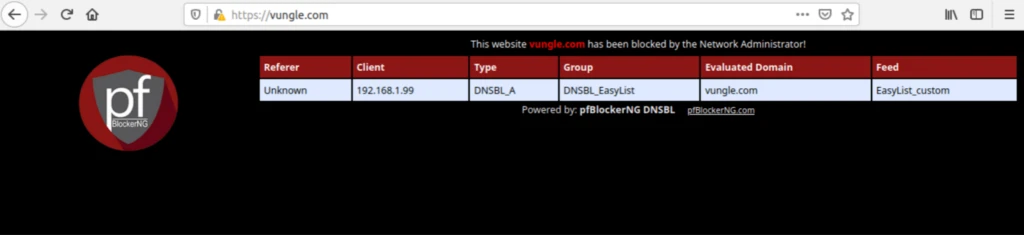
Testing DNSBL
To ensure that DNSBL filtering is working, we will try to connect to the domain I added to DNSBL Custom_List: vungle.com. If I try to access vungle.com in my browser, the DNSBL block page is displayed with some bits of helpful information.
Note: pfBlocker’s DNSBL includes a mini web server that can serve this block page. IPv4, IPv6, and GeoIP filtering extend the existing functionality of the pfSense firewall and block or allow IP addresses without displaying a block page.
Wrap-up
So there you have it. You’ve successfully installed and configured pfBlockerNG-devel in pfSense. We configured IPv4 filtering, GeoIP filtering, as well as DNSBL filtering. All three of these make your network more secure and private without slowing down your connection.
As your network grows, you may need to open certain ports on your WAN if you want to run a VPN server or if you want to host a web server that’s accessible from the internet. When you do that, pfBlockerNG will be a nice tool in your security toolkit to help you lock down your network and granularly control access from the outside.
No Comments